Bring Better Information to the Authentication Moment
How Aligned Trust Creates the Global Trust Layer
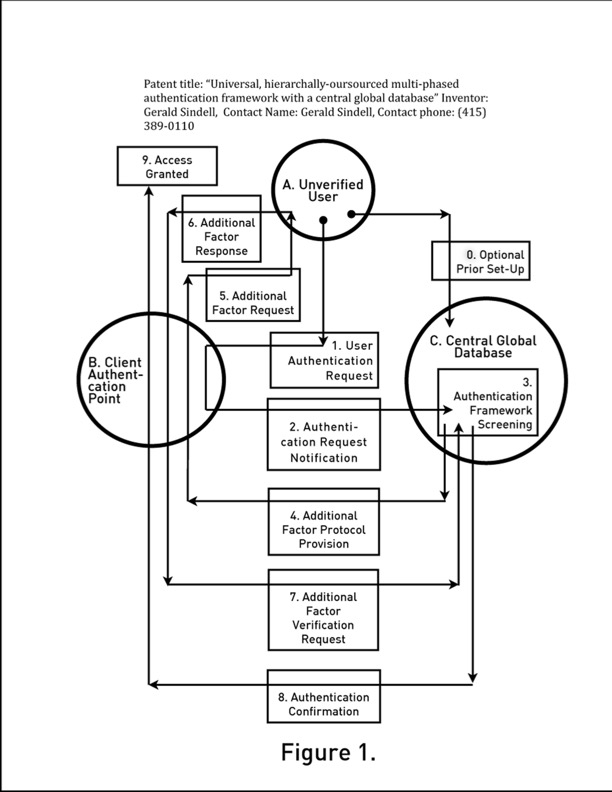
Everything’s at risk in that fraction of a second. Within this seemingly simple architecture the revolution emerges.
Non-Disruptive Over-the-Shoulder Architecture
Defensive crouch? Or confidence based on actually knowing?
The old state-of-the art is ring-fencing – build a higher wall.
Hint: it will never be high enough.
1
Initiate Secure Access
The customer initiates authentication the usual way, entering their credentials into your existing interface. Aligned Trust is invisible to your customer.
2
Dynamic Verification
Most of the time, we already know your customer and whether it is actually them attempting to authenticate, no second factor required. We give the go-ahead and that’s it! You grant access. If we aren’t certain, we put up a flag.
3
Access Granted
Once verified, your customer is granted immediate access without additional steps, streamlining their experience.
Patented Breakthroughs
How many insects are in this picture?
No more captcha. No more six-digit codes. No more ‘Remember me on this device’ which never works anyway. Suddenly, the world’s a better place.
Phishing Resistance
CEO gives away the keys? No problem. With Aligned Trust in place, the imposter is offered a challenge that they simply can’t fake.
Seamless Integration
Our system integrates effortlessly with existing infrastructures, enhancing security without disruption.
Scalable? Designed to protect the whole world…
From Day One, we have built in global capacity as a fundamental requirement for our systems and capacity.